Write secure software from the first keystroke
SecureFlag, a developer's blueprint to integrating security from the first keystroke.
Top 10
Security
Vulnerabilities
Security
Vulnerabilities
Security Misconfiguration
Vulnerabilities
Vulnerabilities
Security Misconfiguration
Vulnerabilities
Vulnerabilities
Software and Data
integrity Failures
integrity Failures
Broken Access
Control
Control
Injection
Vulnerabilities
Vulnerabilities
Insecure Design
Vulnerabilities
Vulnerabilities
Identification and
Autentification
Autentification
Vulnerable and
Outdated Components
Outdated Components
Security Logging and
Monitoring
Monitoring
Cryptographic
Failures
Failures
Server-side Request
Forgery
Forgery

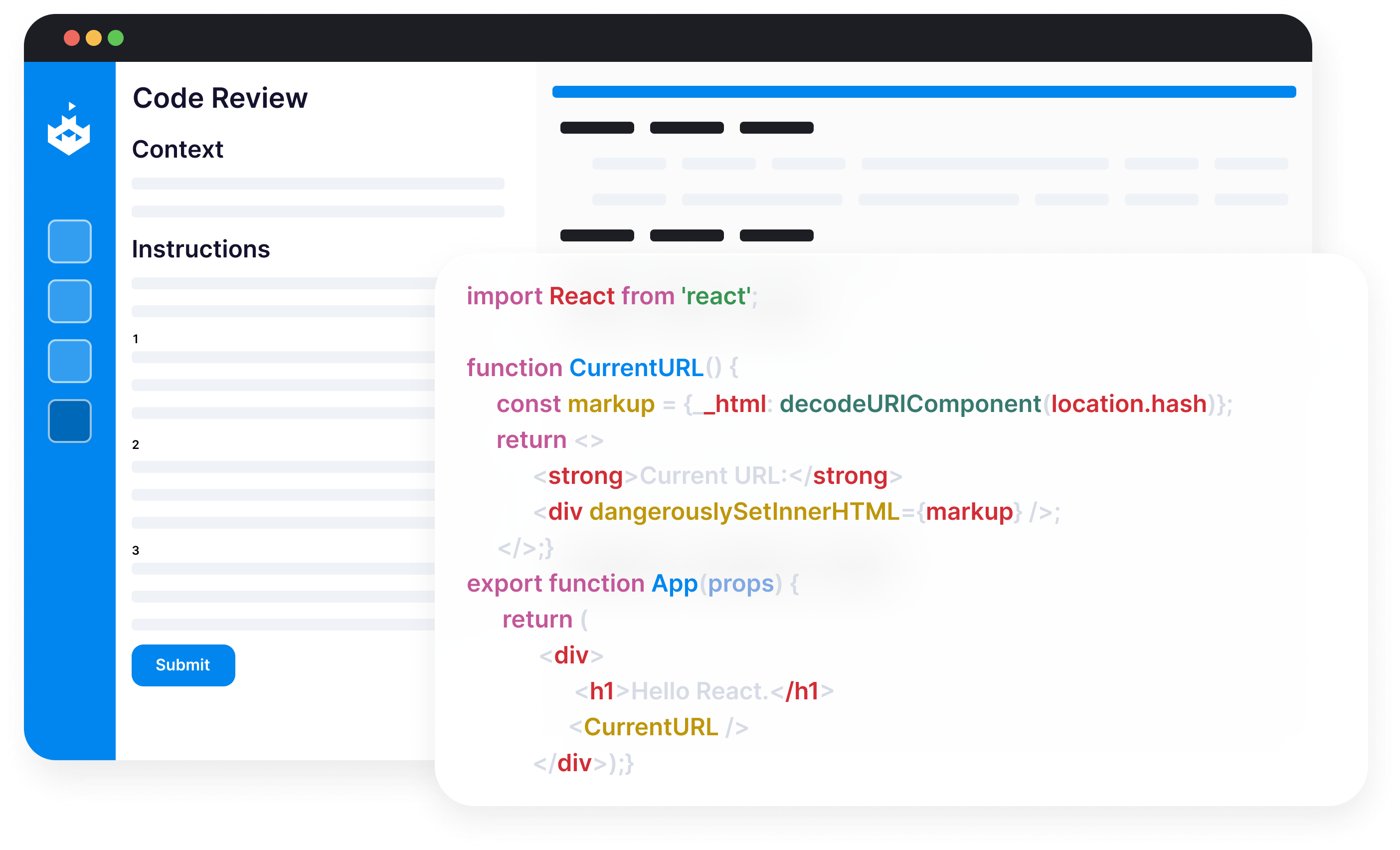
Secure coding Best Practices
Input validation
Input validation is a foundational security measure that ensures only appropriately formatted data enters a system. Proper input validation acts as the first line of defense, preventing malicious actors from exploiting unintended behaviors of a system.
Least privilege
The principle of least privilege advocates for granting only the bare minimum access or permissions necessary for a task. By ensuring that systems, users, or processes operate with as few privileges as possible, the potential damage from accidents, errors, or breaches is limited.

Secure defaults
Secure defaults refer to the practice of ensuring that the initial settings of systems and applications are as secure as possible out-of-the-box thereby reducing the potential for configuration errors or overlooked vulnerabilities.
Avoiding Components with Known Vulnerabilities
Even the most secure system can be rendered vulnerable if its foundational components are flawed. By staying updated with the latest patches, updates, and quickly fixing components with known vulnerabilities, organizations can maintain system's integrity and defend against potential risks.
Keep Security Simple
Complexity is the enemy of security. A simple, streamlined security design is easier to review, maintain, and understand, which leads to fewer errors and vulnerabilities. Adhering to a philosophy of simplicity in security design helps in achieving robust and efficient protection.

SecureFlag’s Secure Coding Training platform
SecureFlag offers thousands of hands-on labs for 45+ technologies
covering 150+ security vulnerabilities
Discover our platformcovering 150+ security vulnerabilities